- Forget AirTag: This Bluetooth tracker is my top pick for both iPhone and Android users
- This midrange robot vacuum cleans as well as some flagship models - and it's 50% off
- You may qualify for Apple's $95 million Siri settlement - how to file a claim today
- This 3-in-1 robot vacuum kept my floors clean all season, and it's priced to compete
- I changed 6 settings on my Roku TV to give it an instant performance boost
How to Secure AWS Serverless API(s)
Network Security
Discover how to easily enhance security of your container-based AWS serverless API to protect against known and unknown vulnerabilities.
Read time: ( words)
Container-based serverless APIs are becoming increasingly popular as many organizations move toward cloud native applications. Serverless containers outsource the effort of managing the actual servers, making it easier to scale quickly and maintain at any scale. However, you are still responsible for protecting your public APIs from being exploited by known and unknown vulnerabilities.
I am going to show you how to enable additional security protection for serverless container-based APIs with Amazon ECS and Amazon API Gateway, based on this architecture:
Source: AWS Architecture Blog
By deploying Trend Micro Cloud One™ – Network Security, visibility of network traffic across your enter architecture will dramatically increase, enabling security operation teams to quickly detect and investigate suspicious behavior without impacting developers’ workflows.
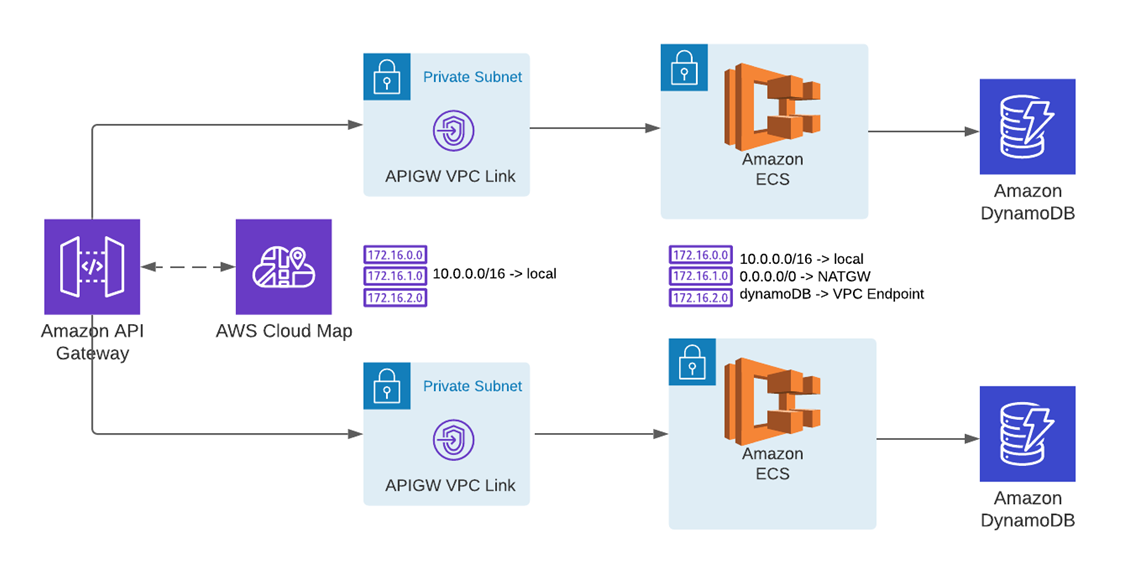
Serverless container-based API architecture overview
As you can see above, there are two services created: petstore and foodstore. Both services are running behind API-Gateway and are enabled to receive PUT and GET requests. Unauthenticated users can only send GET requests whereas authenticated users can send both GET and PUT requests. In this example, Amazon Cognito is used to perform user authentication, Amazon DynamoDB for persistent storage, and Amazon ECS to host the services.
Amazon ECS services are running in a private subnet and API Gateway uses a VPC link (APIGW VPC Link in the diagram) in order to connect to them. APIGW VPC Link and Amazon ECS services are running in the same subnets (per availability zone).
By using Amazon VPC Routing Enhancements, we can now easily intercept traffic coming from API Gateway to APIGW VPC Links and send it for inspection, making sure that only clean traffic reaches ECS services.
In this example we are going to send the traffic coming from API Gateway for inspection to a Security VPC, with a Gateway Load Balancer (GWLB) deployed together with a fleet of Trend Micro Cloud One™ – Network Security appliances. We will create a Security VPC in your AWS account by using an AWS CloudFormation template.
To follow along with this article, you can sign up for a free, 30-day trial of Trend Micro Cloud One™.
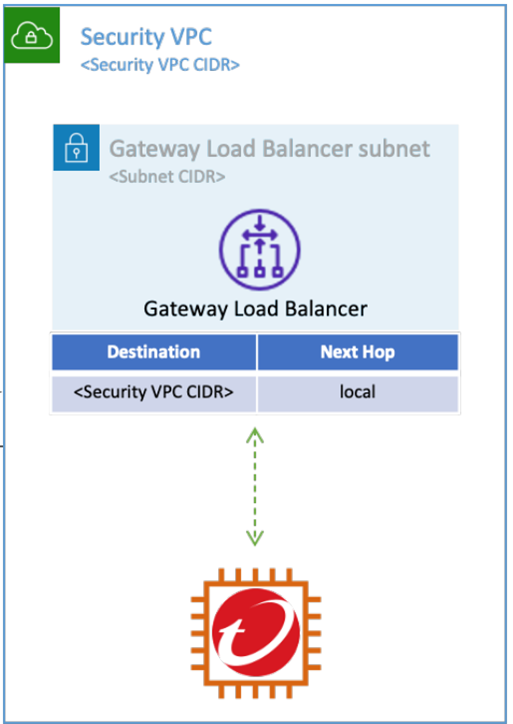
Create Security VPC in your AWS Account
You can use ready-to-deploy CloudFormation templates to launch Security VPC stack in your AWS Account. The templates will create a new Security VPC and all resources required for traffic inspection, like subnets, Network Security appliances, GWLB, etc.
The following diagram shows the architecture of the Security VPC automatically created by CloudFormation templates.
To create Security VPC resources, first create a new Macro CloudFormation stack:
1. Select Launch Stack by clicking on the button below:
2. Leave any parameters on their default settings, then click Create stack.
3. Wait until the stack transitions to “CREATE_COMPLETE” state.
Secondly, create a new Security VPC Stack:
1. Select Launch Stack by clicking on the button below:
2. Refer to Trend Micro Cloud One documentation for more information regarding stack parameters values.
Prepare your environment to inspect traffic
Before sending traffic for inspection to you Security VPC make sure to move APIGW VPC Links to separate subnets. Refer to the diagram below to see how the infrastructure will look like at this point.
If your APIGW VPC Links are already in separate subnets in your real environment, you can skip this step.
Next, you need to create one subnet per availability zone for GWLB endpoints, which are used to intercept traffic and route it to Security VPC. Make sure to use a small CIDR block like /28 for these subnets, since you are going to need just one endpoint network interface in each of them.
Now you are ready to enable traffic inspection for your serverless API by automatically sending traffic coming to APIGW VPC Links from API Gateway to Security VPC for inspection. Use Amazon VPC Ingress Routing for this, since it allows us to create more specific routes than the default local route.
Refer to the diagram below to see how the routes should look like:
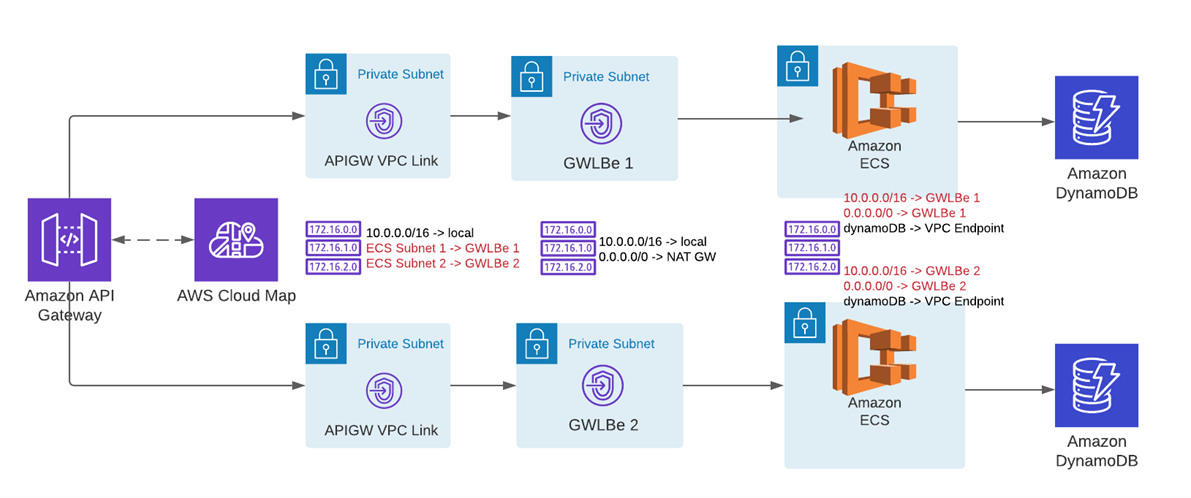
As you can see, all traffic coming to APIGW VPC Link subnets for Amazon ECS subnets will be now redirected to GWLB endpoints, and automatically sent to Network Security appliances for inspection. Refer to the diagram below for a complete setup:
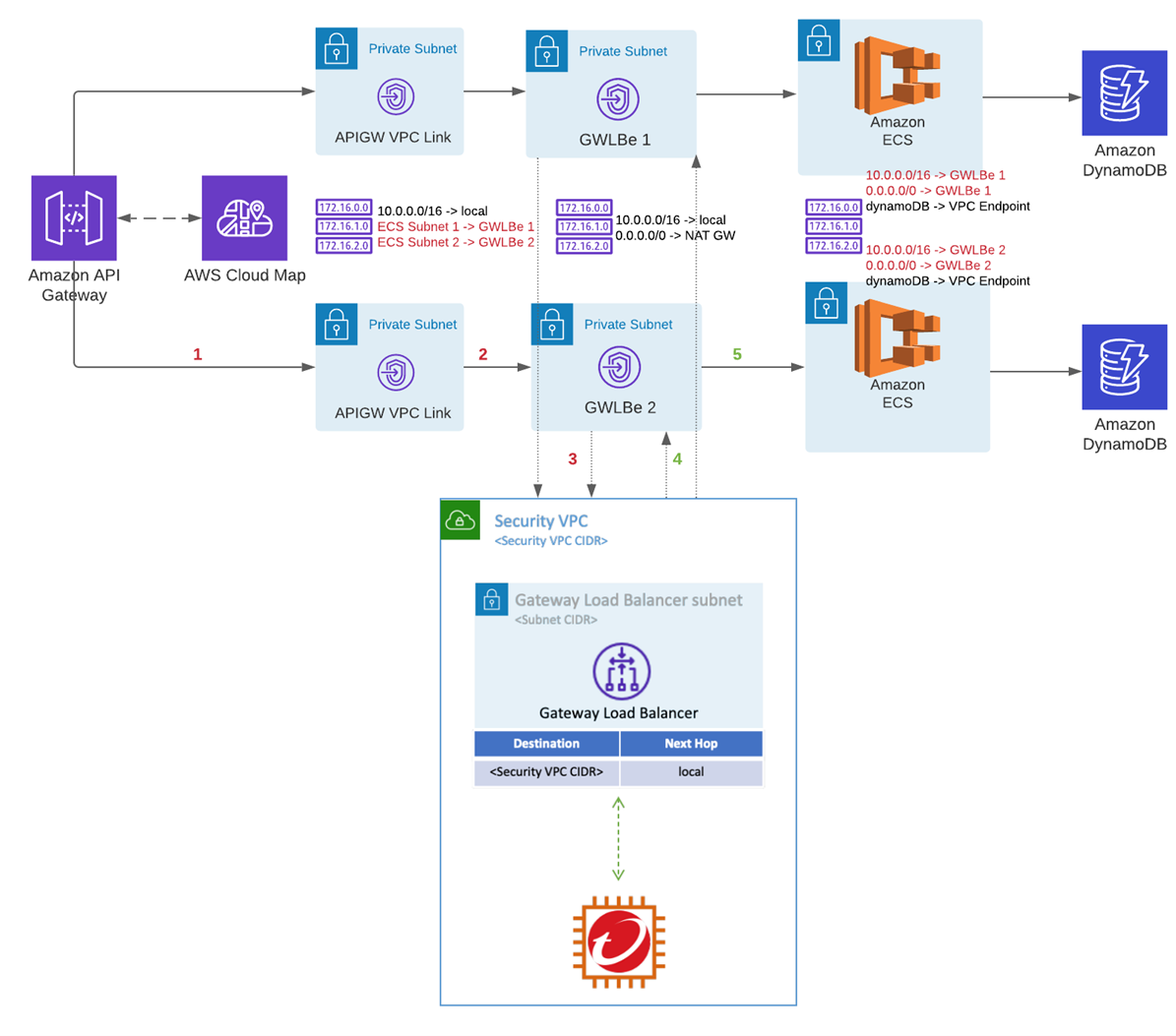
Next steps
Just a couple tweaks to your architecture with Network Security can ensure your container-based serverless APIs are being continuously monitored for known and unknown vulnerabilities. Automated scans of ingress, egress, and lateral movement with customizable post-scan actions help security teams contain and investigate potential threats quickly, which in turn lets developers build quickly. To learn more about Network Security capabilities and integrations with AWS services, check out our documentation.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk



